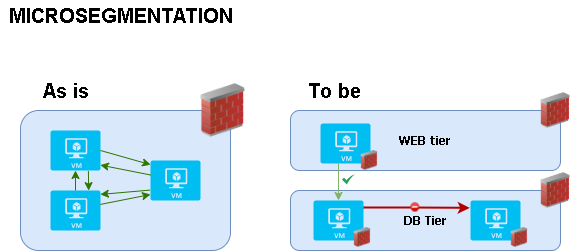
Last year i was involved in a huge project where we needed to make a micro segmentation implementation with a zero-trust approach for more than 1000 virtual machines within 4 months.
Few people from VMware and other companies has asked me how we achieved this and what the challenges was, ups and downs.
First, it was not easy! It was hard work and team effort. The business was involved as well and we had a good strategy to involve the relevant application owners.
Before you begin with the microsegmentation project i will suggest you have following:
- Support from the C-level, this is not done without hard work and some internal fights between teams.
- Invite the whole business to a homemade presentation on how you will approach the micro segmentation project and how it will impact the business and help the business on the journey you are starting.
- If you have a dedicated communication team, let them help you so you can reach the information out to the system owners
- Update the system owner minimum 2 weeks ahead of “enforcement” of their application and after the “enforcement is done”
Did we encounter issues/application downtime?
YES – but not important systems
We started migrating the small not critical systems, we took healthcare, AD, DNS and DHCP at the end of the project so we had a good experience on how the micro segmentation was done.
But how did we do the actual Micro segmentation?
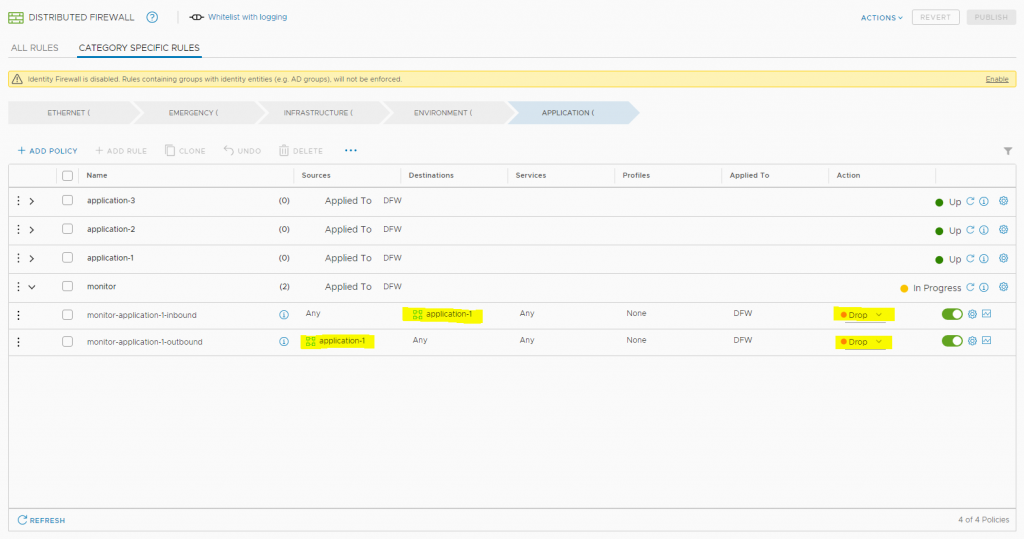
- Begin to make firewall-rules for the application based on flow-analytics from VMware Network Insight
- Started monitor mode – we made a custom made system to monitor for rules where we find traffic not hitting any of the existing firewall rules (to eliminate errors) PASS mode.
We got the information from VMware Loginsight and used a Webhook to pass the logs to our own monitor-alert dashboard. - Informed the system owner for the date and time “enforcement” – min. 14 days ahead
- Monitor mode enabled – handling alerts
- Enforcement – We changed the default monitor rule from PASS to DROP
- Informed System owner
- Monitor mode enabled – handling alerts for the next 14 days
- Removed monitor rules and informed system owner that the system was finish with the micro segmentation.
Below picture shows how the NSX-Monitor dashboard was handled, we had a few monitors running this so we could handle the alerts coming in.
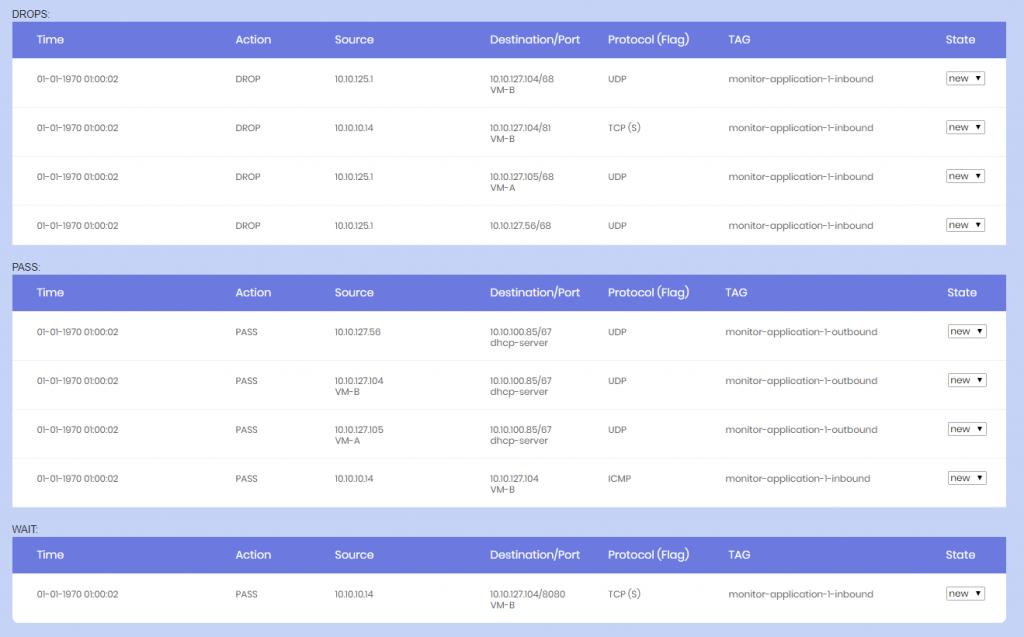
I will in my next blog share the code behind the nsx-alert dashboard and how we did it.